Bad Guys are after you. Well, not really you, but they are after your personal and financial information. Not only that, they are after any personal/financial information you may have for other people.
The most common way they try to get this information is by sending phishing emails, voice or text messages. A phishing attack tries to manipulate you into certain actions or divulging confidential information. Phishing has proven to be a very successful method for attackers to gain unauthorized access to an organization’s information. It is a form of social engineering.
There are six key principles that may be used with any social engineering attack.
- Reciprocity – People like to return a favor. This is why free samples at the grocery store work so well!
- Commitment – If people commit either verbally or in writing to an idea no matter how small, they are more likely to honor the commitment.
- Social proof – People will do things they see other people doing. Ask 3 other people to join you on the corner looking up into the sky. See how long it takes for others to join
- Authority – People tend to obey authority figures, even if asked to do objectionable acts.
- Liking – People are easily persuaded by people whom they like
- Scarcity – Perceived scarcity generates demand. - “Limited time only”offers is an example of this
(For more information see www.wikipedia.org under Social Engineering)
What information do attackers go after in phishing attempts?
- Usernames and passwords – These can be used by the attacker to log into your personal and work email accounts.
- Email addresses of colleagues, family or friends – Often used to send more convincing emails to them.
- Personally identifiable information (PII) – Names, physical addresses, birthdates, Social Security Numbers, etc. These all can be used for identity theft.
- Financial information – Credit card numbers, bank account information, tax records or W2s can be used to commit tax fraud and steal money.
- Medical or health insurance information – often used to commit healthcare insurance fraud.
How does phishing work? Typically, the attacker will send an email or text message to a user to try to persuade the user to do one of the following:
- Reply to the message with the information requested.
- Click a link to visit a fraudulent website, then enter a username and password.
- Download an attachment which then executes a malicious program.
- Click a link to visit a compromised website which causes malicious software to run on the computer.
There are several things you can look for with an email to identify a phishing attempt:
- Does the email offer something that looks too good to be true?
- Are you expecting this email from someone you know/trust?
- Does the sender try to impersonate a reputable person/organization?
- Are there offers of gifts or money?
- Does the email want you to take action now or try to trigger some emotion?
That’s pretty theoretical, right? Maybe an example would help!
Here’s an example phishing email. Let’s look at some phishing indicators and ask some questions…
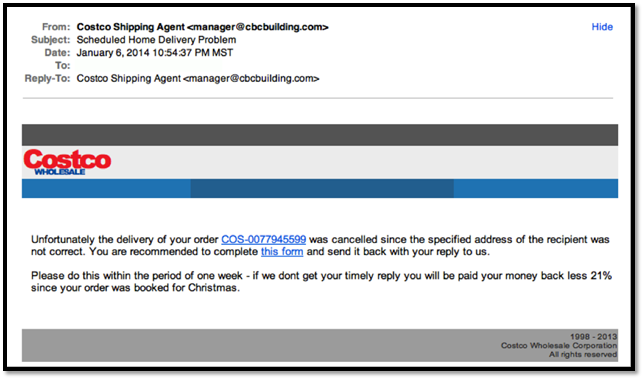
- If you did not have an outstanding order from Costco, then you should assume not legit.
- Take a look at the From: email address – manager@cbcbuilding.com. Nothing in that email address indicates it is a real Costco email address. You would probably expect something like @costco.com.
- Note the urgency and loss of 21% in the last paragraph. Phishing emails often want to you act now and trigger an emotion – Oh, no! I’m going to lose my money!!!
- There are a couple of links in the body of the message. We cannot see it here, but those links direct you to a website that looks similar to Costco but is not, and then asks you to log in with your CostCo username/email address and password. It is an attempt to harvest your credentials.
Now that we’ve seen some things to look for, what should you do if you receive a suspicious email or text message?
- First off, be patient as you evaluate the email or message for legitimacy.
- Don’t instantly click any links! Should you expect links? Hover over the link to see where it goes. Does something feel “off”?
- If you are unsure, check with a coworker for their input.
- Hover your pointer over the From: to see the sender’s email address. Is that an address you interact with?
- Look for emotional triggers that try to get you to do something right now.
- When you decide that the email is a phish, forward that on to your technology or security group, as they may implement a filter to keep others from receiving that email.
- Finally, don’t be afraid to just delete that email!

